IEEE Reliability Society Newsletter Vol. 56, No. 2. May 2010
Front page:
President's Message
From the Editor
Society News:
Stay Connected With Your Reliability Society:
Facebook, Yahoo Groups and LinkIn
AdCom Elections:
Call for Nominations
Awards: Call for Nominations
Feature Article:
Security and Fault Tolerance-
a Cmap
Chapter Activities:
Dallas
Chapter
Joint Boston, New
Hampshire, Providence Chapter
Denver Chapter
Cleveland Chapter
Technical Activities:
Annual Technology Report
Announcements:
Prognostic Health Management Conference -
Announcement and Call for Papers
IEEE SmartGrid
Conference
Call for Papers
Green Technology Reliability Seminar
Safety & Reliability Workshop
Security and Privacy Magazine:
Call for Papers
Distinguished Lecturer Program:
Call for RS
Distinguished Lecturers
Reliability Society Newsletter - May 2010 Feature Article:
Security and Fault Tolerance —
a Cmap
by Goutam Kumar Saha, Senior Member, IEEE <gksaha @ ieee.org>
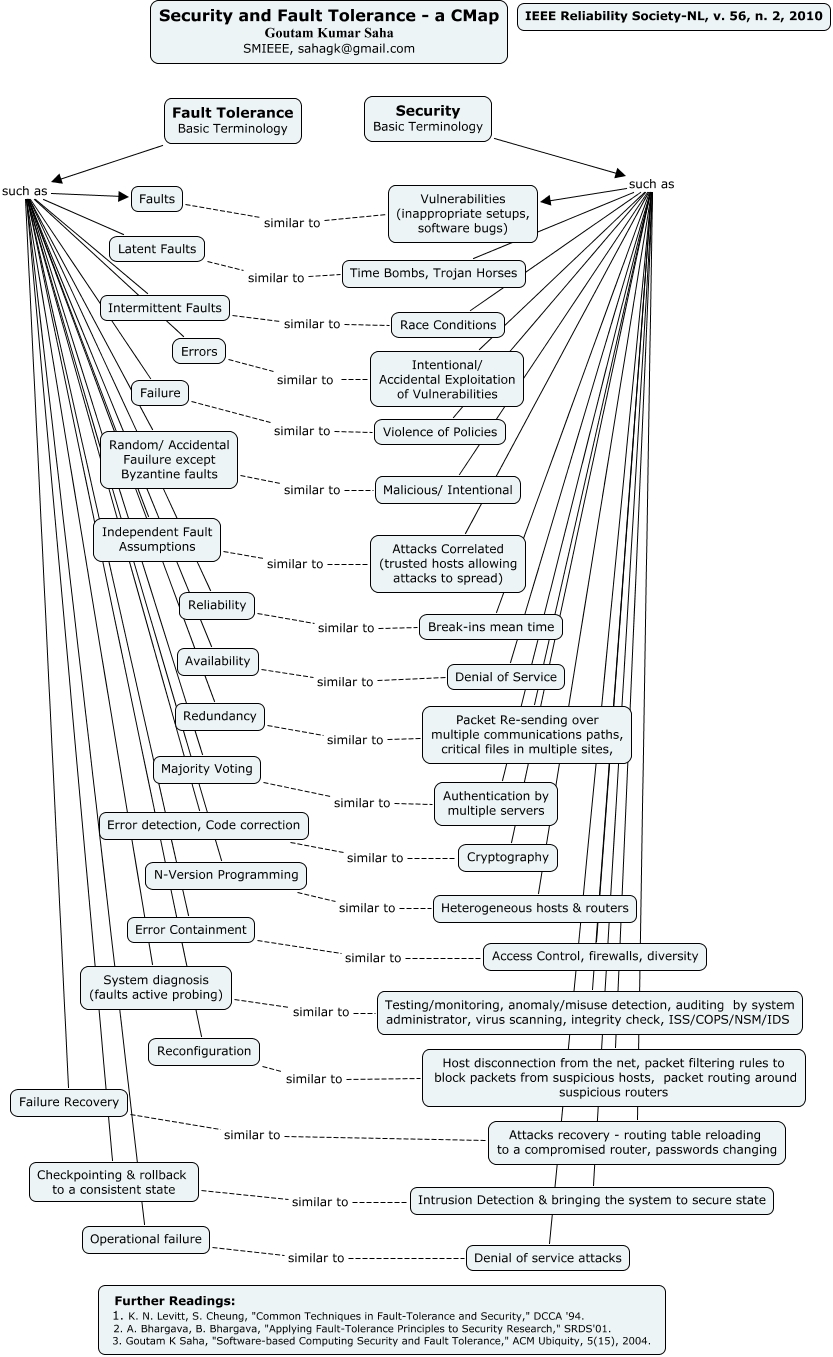
This article aims to visualize the similarity among the terminologies of security and fault tolerance through a concept map or knowledge graph. Concept map is a two-dimensional representation of cognitive structures showing the hierarchies and the interconnections of concepts involved in a discipline or a sub-discipline. Concept maps have the purpose to harness the power of our vision to understand complex information "at-a-glance." Each node typically represents a concept, and an arc between two nodes represents a relationship between two concepts.
Reliability is a key requirement in fault tolerant systems design whereas security is through retrofitting such as firewalls and intrusion detection. Security terminology- vulnerabilities due to software bugs or incorrect setups are similar to the term faults in fault tolerance. The terms Trojan horses, time bombs may be considered similar to the term- latent faults. Race conditions correspond to intermittent faults. Intentional and accidental exploitation of vulnerabilities are similar to the term- errors in fault tolerance. Policies-violence may be looked as the term- failure. Intentional or malicious attacks correspond to random or accidental failure. Correlated attacks correspond to independent fault assumptions. Break-ins mean time is similar to reliability. Counterpart of the denial of service is availability. Packet resending over multiple communication paths is similar to the term- redundancy. Multiple servers' authentication is similar to the term- majority voting. The counterpart of the term cryptography is error-detection, code- correction. The term heterogeneous hosts and routers are similar to N-version programming in fault tolerance. Security audit, testing, monitoring might be similar to system diagnosis. Counterpart of packet routing around suspicious routers, host disconnection is system reconfiguration in fault tolerance. Attacks recovery has its counterpart failure recovery. Counterpart of intrusion detection and bringing the system to a secure state is check pointing and rollback to a consistent state. The term- attack causing denial of service is similar to the term operational failure in fault tolerance.
Further Readings:
[1] K. N. Levitt, S. Cheung, "Common Techniques in Fault Tolerance and Security," DCCA'94.
[2] A. Bhargava, B. Bhargava, "Applying Fault Tolerance Principles to Security Research," SRDS'01.
[3] G. K. Saha, "Software- based Computing Security and Fault Tolerance," ACM Ubiquity, 5(15), 2004.
[4] G. K. Saha, "Understanding Dependable Computing Concepts," ACM Ubiquity, 8(44), 2007.